The Best Fortification For IPC & IoT Devices
As a leader in industrial PC design, Qbic’s primary goal is to help our partners build the most reliable and safe products. After years of research and development in the security scope, we are excited to announce the Qbic Fortify+, which provides our partners with easy integration of Qbic customized security features into products and services for secure-critical projects.
The Security Trinity
In device security, device access, data usage, and operating environment are interactive, and the protection of those three aspects is indispensable. Qbic deploys nine major fortifications for partners to prevent devices from security threats
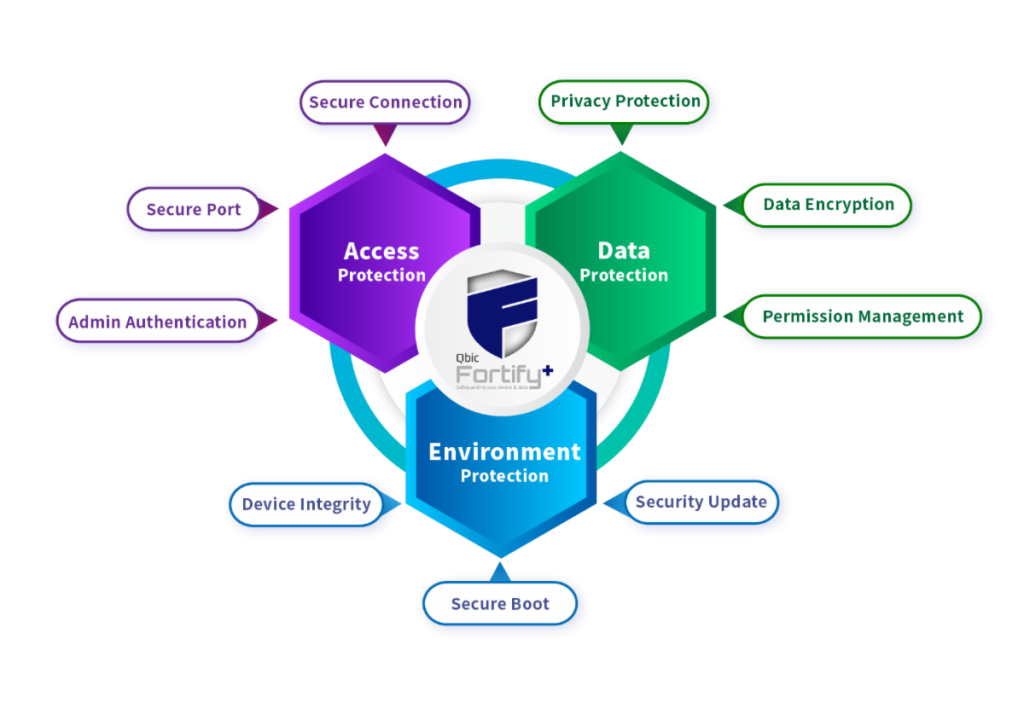
Access Protection
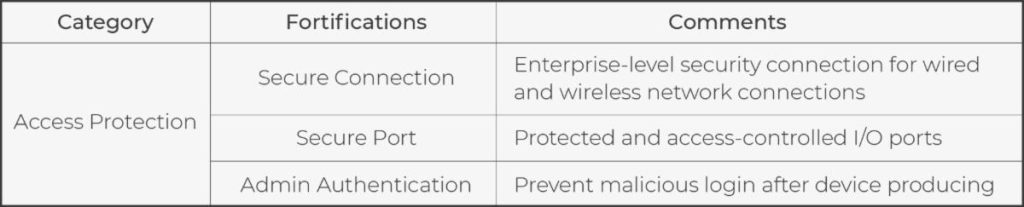
The first step in most attacks is obtaining access rights, whether remote access or physical access. Qbic Fortify+ allows MIS/IT to define physical and remote access with constraints in advance to fit different user scenarios. Furthermore, encrypted connection is required, especially in remote access. Besides the access via network and I/O ports, the protection for the login process is ignored easily. An authentication mechanism for the device administrator can be pre-set up in the production process. Therefore, security during device delivery is not compromised. After passing all enhanced security passes, the device will deliver the access rights finally.
Data Protection
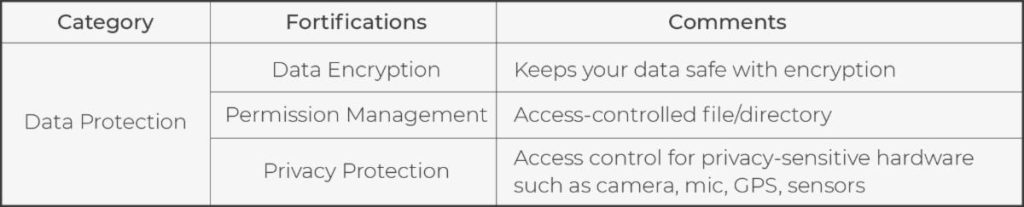
Nowadays, information protection has become an essential requirement, especially in the IoT environment. Hackers can steal or misuse information through local or remote access. Though access protection of Qbic Fortify+ provides the first layer protection, Qbic still deploys the second layer protection: data protection to ensure information security. Encrypting data and limiting access are the most popular methods to provide information security. But these only satisfy general usage. For example, within the control center of an automated factory or government institutions like the Department of Defense, sensitive data such as image/video, voice, and environment status are supposed to be protected well. Therefore, cameras, mic, GPS, and kinds of sensors should be accessed restricted.
Environment Protection
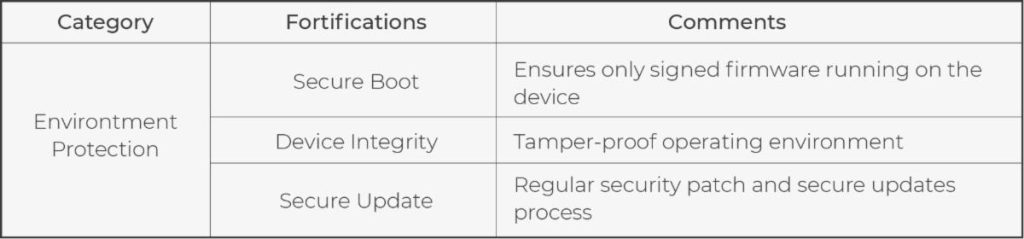
In the environment protection of Qbic Fortify+, firmware is the first target to be protected. Due to the system update being enabled in most situations, replacing the whole system becomes a practical attack method. But don’t worry; Qbic Fortify+ deploys three checkpoints to defend against this attack. First, the attacker needs to pass the access protection. Second, even the hacker gets the access right and then injects the malware files into a device, those files need to be certified before the upgrade process. Finally, the boot loader plays the goalkeeper. The device will not start successfully if the updated system is not approved. Besides the firmware replacement attack, APPs and configuration are required to be safeguarded. Qbic’s customized firmware provides environment pre-build, such as APPs pre-install and Wi-Fi access pre-setting. Thus, limiting related changes can maximize the system’s robustness. Finally, security patches will be provided regularly for devices to reduce the probability of being attacked. Of course, the patch files are transferred via a secure tunnel, just like the firmware upgrade. Thus, the entire operating environment is protected.
The Pursuit of Security Never Ends
In the future, new hardware and software vulnerabilities will be discovered continuously. Therefore, the Qbic Fortify+ is just a milestone, not the final destination of Qbic Technology in security scope. Qbic’s primary goal is to help its partners build the most reliable and safe products and services. And, we never stop.